Mobile app security issues are critical for any developer. The user needs to trust that the app they are using is safe and does not have any vulnerabilities that could unwittingly expose them or their personal data to malware. A compromised mobile app can expose the device to viruses, freeze or disable device functionality, or even wipe a user’s personal information from the device.
Why Mobile App Security Testing is Important?
Testing for mobile app security is important to make sure your app is functional and secure. You should consider a variety of security tools to combat the growing threat of mobile app data breaches. Testing can include technological and individual means to preserve the integrity of a mobile app. Treat your client’s data with the same high standards that you would treat your own.
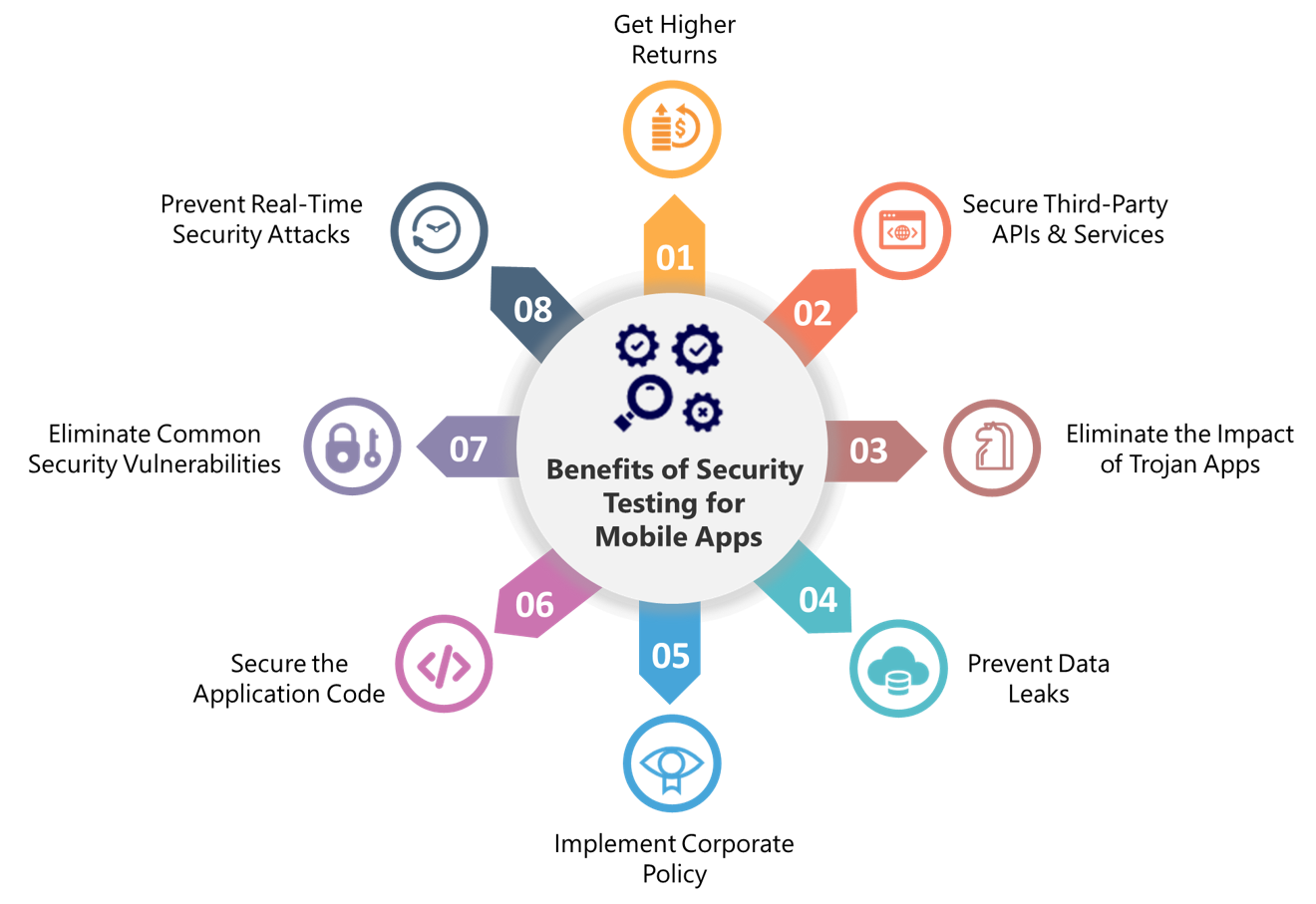
Challenges in Application Security Implementation:
In this section, we discuss the familiar challenges that developers and testers might face in building a secure product.
1. Inefficient use of security tools:
Developers find testing during development and hence cannot use enough tools to test their code. On the other end, 1-2 tools are not enough to catch all the vulnerabilities at once.
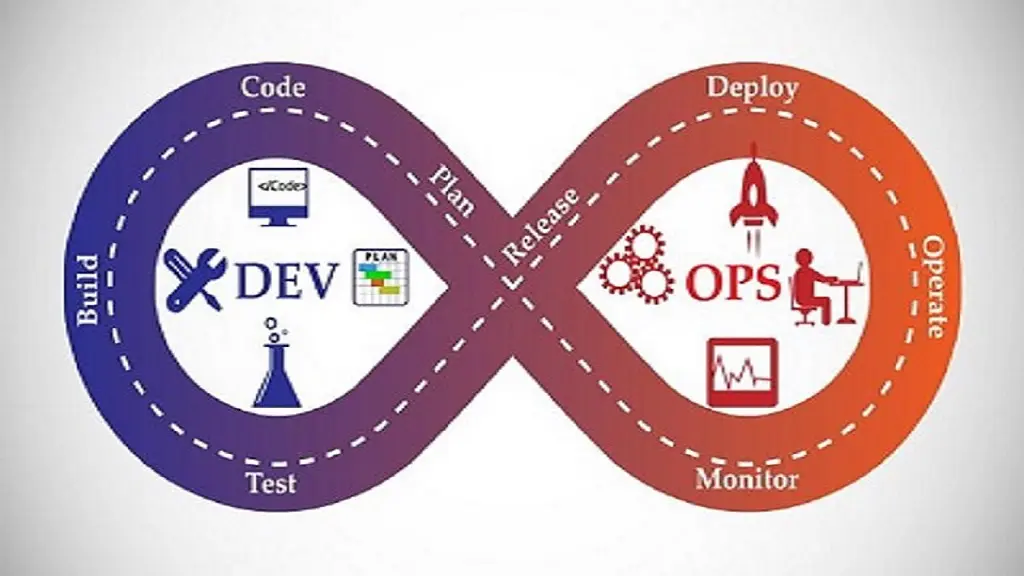
2. No DevSecOps approach:
DevSecOps approach is particularly important if you want to follow the best security implementation practices. It is an approach that includes development, security, and operations simultaneously.
3. Open-Source Vulnerabilities:
Open-source systems have more vulnerabilities. These vulnerabilities made these systems prone to foreign attacks. These vulnerabilities include poorly written code, careless integration of components, lack of security functionalities, and infrequent updates.
Mobile App Security Best Practices/Checklist
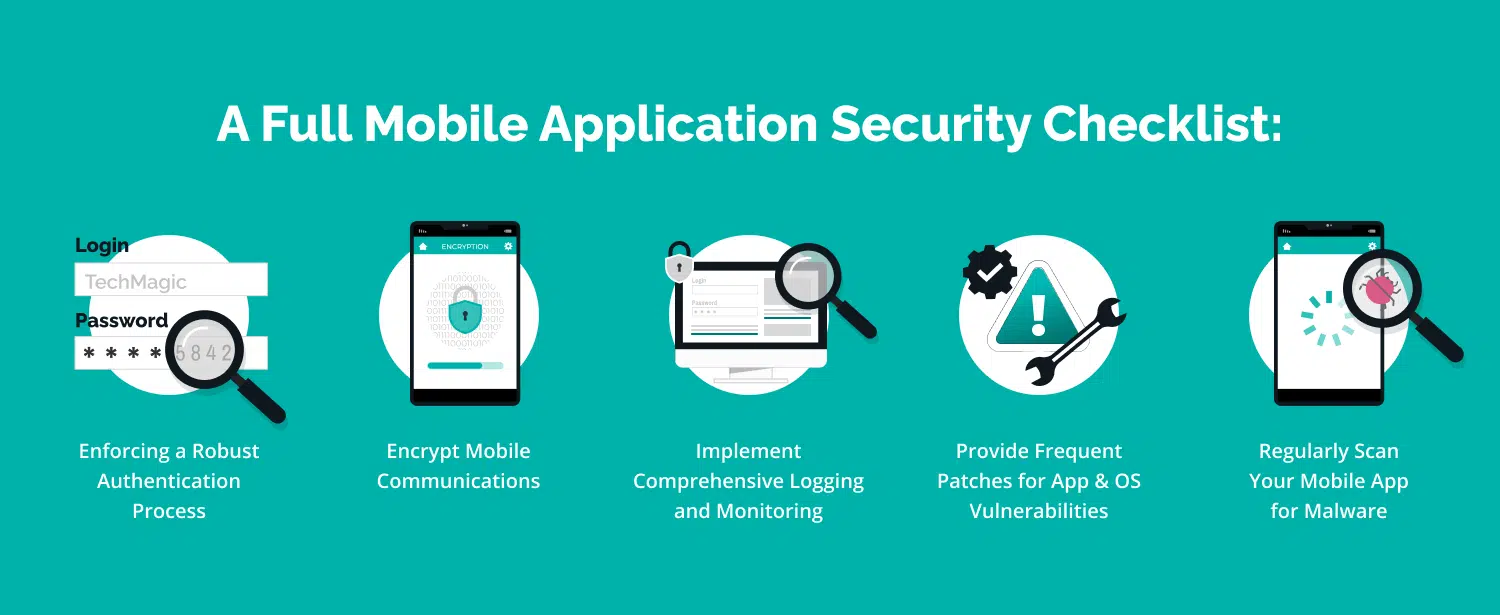
There are steep expectations for mobile app developers. Current and future development has a heavy dependency on getting it right the first time. Instead of hoping updates fix the problem, developers should make a mobile app security standards checklist based on efficiency.
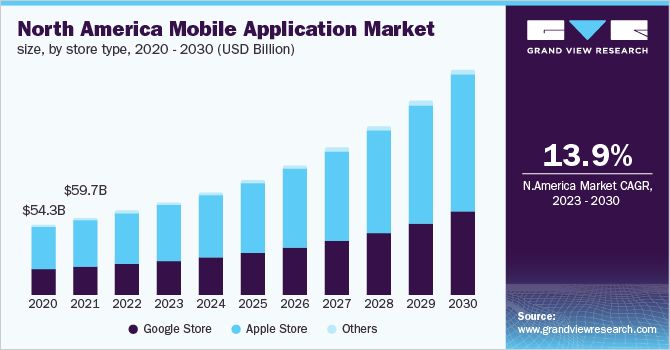
The growth of mobile applications is expected to reach $935 billion (about $2,900 per person in the US) (about $2,900 per person in the US) by 2023. There is a significant rise in iOS and Android app development market.
Here we have 10 points mobile app Security Standards/Checklist to Consider During App Development. The ten things below should be on the radar of any mobile app development team that wants to put out the best product possible.
1. Keep The Source Code Secure
There is a secure code, and then there is secure code. Apps that are a direct port from another platform will have a lot of holes. If you want to leave the source code open, then there will always be risks since it is often exposed on the client side. Working as open-source requires you to take a long look at the business logic of mobile app security.
Even if the source code gets into the wrong hands, it should not be a major red flag if the code is secure. Obfuscating the code is one way to secure it, and will get rid of a lot of low and mid-tier troublemakers.
2. Plug Communication Holes
Making sure communication is more secure starts by protecting the transmission of data. This is something that even top tier mobile application security suffers from, and can be one of the hardest parts of development. Fancy military grade encryption means nothing if it isn’t implemented properly, especially at the root level.
Communication holes are taken care of by using VPN, Https, SSL, and TLS. These protocols should be on the drawing board at the conception level instead of tacked on at a later date. Even if a hacker breaks through normal security, they won’t be able to translate the data received. This neutralizes even the most severe security threats that make it past the first line of defense.
3. Enhanced Data Portability
Data that is confined to a single platform or service is wasted data. Adding portability to that data will give you much better options for long-term security, marketing, and bug fixes. Data portability has become a special talking point since the introduction of social media connections.
Being able to sign in and automatically share data cuts down on time, and prevents useless data from accumulating. Having to match the data of the same person across six different accounts is both annoying and counterproductive. When mobile app developers introduce an easy way to log in and share data, it provides a confidence boost to the client.
4. Database Security
Database security goes far beyond securing the source code. Whatever data is entered into a website or app needs its own set of security since this involves the client’s data. Payment information or user credentials are something that should never be left to chance.
That means securing things from both ends, and ensuring that both the app and its hosted platform are up to date. Breaches with the database are not the end of the world if secure code and communication practices are followed. But that doesn’t mean you ever want it to reach that point.
5. Can The Product Be Reversed Engineered?
Open source applications can be reversed engineered to reveal vulnerabilities. This is more of an Android problem than iOS, and puts a lot of stress on developers to protect their applications. Engineering from the ground up without taking a lot of shortcuts can slow down, and sometimes prevent reverse engineering.
When a lot of recycled code from other projects are used to make up the bulk of new mobile apps, it becomes a target for reverse engineering. New and protected code is needed, and is considered a good idea for most projects. If old code has to be used, then make sure that previous security protocols are looked over and enforced.
6. Cryptography Using Common Sense Methods
Cryptography is how to secure your mobile app with minimal resources. But across many mobile applications, improper cryptography is a rising concern. This lowers the overall security of the application while putting the client’s data at risk.
Cryptography can provide a false sense of protection when it isn’t implemented properly. Weak algorithms won’t magically become usable, even if it is implemented in a solid framework. When done right, cryptography will protect user’s data and the application.
7. Protect Authentication And Authorization Systems
A strong authentication and authorization system should be at the core of any mobile app security checklist. Device security, session management, identity management, and privacy have a strong reliance on one another.
If one of them is weak, then the others won’t be as effective. All of these systems are already included in basic apps like web browsers. Not including them in your checklist for a modern app is a grave oversight. By itself, lack of privacy is something that can torpedo the usefulness of a mobile app.
8. How Well Does The Product Fit In With The Platform?
Android and iOS are the two biggest mobile platforms in the world for mobile app development. Blackberry OS is still in the wild but is no longer considered to be part of the big boy group. There is also Windows 10 mobile and many other smaller platforms, so options are vast when you go beyond the big two.
Companies don’t have the resources to produce for every mobile platform, so early decisions need to be made about mobile apps. Different security risks are apparent on each OS, so porting an Android app for iOS is like starting from the beginning of the development stage. The type of OS developed for demands a different security protocol or set of patches.
9. Multiple Input Validation Methods
Data can be manipulated, so adding in multiple ways to validate that data is helpful. Ease of use is important, along with a high degree of compatibility. Not all mobile hardware has a fingerprint scanner. And believe it or not, not every client uses a front-facing camera.
Input validation should never come at the cost of speed or compatibility. When you force a validation method that is hardware dependent, it locks out a large portion of your user base. A mobile app that goes down this path will find it hard to right the ship at a later date.
10. The Usual Pen Testing
Penetration testing is still the most effective way to test for vulnerabilities with mobile app security testing. Think of it as the benchmark test every app should go before getting released as a finished product. No matter how rock solid the development process is, the app will always have a few flaws that need to be dealt with.
When penetration testing is avoided, you never get the chance to find out what those flaws are. Clients should never be treated as beta testers for an app that is meant to protect their data.
Final words on mobile app security
Clients have high expectations for security, and value products that respect their time. Data is invaluable at all levels, so there will always be a need for mobile security. Instead of striving for mediocre, developers with a vision will always knock it out of the park.
To summarize the article here are the most important practices to keep in mind while developing an app from scratch.
- Keep the source code secure: reconsider whether to make the code open-source
- Protect data transmission
- Make it easy to log in and share data
- Secure the source code and the client’s data
- Reverse engineer, the code to identify potential vulnerabilities
- Do cryptography right
- Protect authorization systems to protect user privacy
- Make sure the app has the right security protocol or patches for the system
- Add multiple ways to validate data input
- Perform penetration testing
Our experts can help you in developing your next world-class apps.
Why do you consider JumpGrowth to Hire app Developers and Testers?
JumpGrowth is a leading software development company. We always ensure the security of our client’s products. Our testing services include several types of testing such as:
- Functional Testing
- Load & Performance Testing
- Multiple Platform & Devices Testing
- Web Services Testing
- Security Testing
- AR/VR Testing
- Automation/ Automated Testing Services
Frequently Asked Questions:
1. Can I update my mobile app’s security measures after release?
Yes, we can update mobile application after its release.
2. Are there any legal implications for not implementing these security items in my mobile app?
Here are the top 8 legal implications we need to take care of to make our application legal:
- Confidentiality agreements
- Incorporate a business
- Privacy policy
- Terms of Use
- App store agreements
- Intellectual property rights
- Jurisdiction
3. How JumpGrowth help in implementing these security items in my mobile app?
JumpGrowth can pass your application into several types of testing methods such as penetration testing, Functional Testing, Load & Performance Testing, Multiple Platform & Devices Testing, Web Services Testing, Security Testing AR/VR Testing, and Automation/ Automated Testing Services.
4. Can I update my mobile app’s security measures after it release?
Yes, you can update your mobile app’s security measures once it has been released to the public.
Related Blogs: