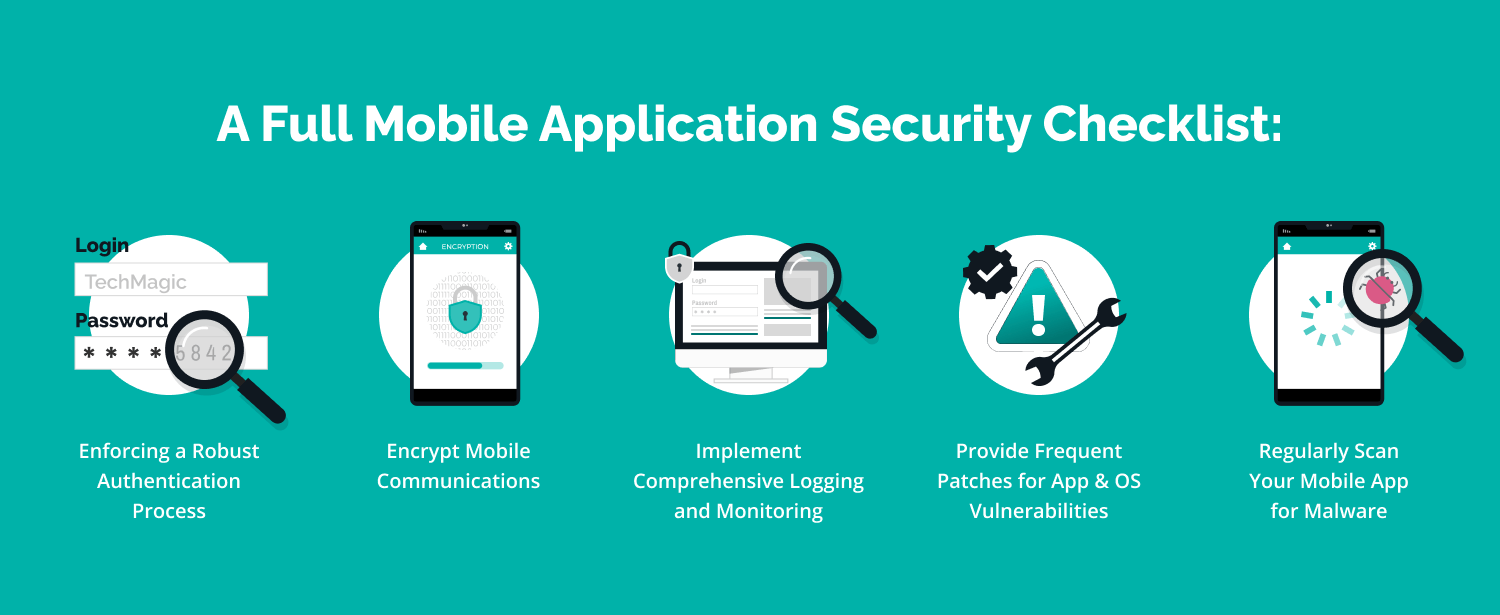
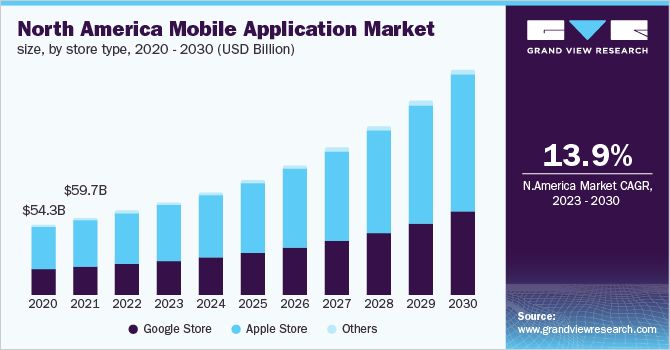
- Services
Product Engineering
Empower your business with cutting-edge digital solutions that drive innovation and seamless customer experiences
Hire
Build your dream team with expert staffing solutions that match top talent to your unique business needs
Cloud
Leverage secure, scalable cloud solutions to streamline operations and unlock new opportunities
Growth
Accelerate your success with tailored strategies and solutions that scale your business efficiently
Artificial Intelligence
Discovery
Onshore Engineers
Gain direct access to top-tier engineering talent in the USA, ensuring seamless collaboration, real-time support, and in-depth industry expertise. Our onshore engineers provide localized solutions tailored to your business needs, enabling faster project execution with minimal communication barriers.
Nearshore Engineers
Benefit from skilled engineering professionals in Mexico, combining the advantages of cost efficiency, cultural alignment, and convenient time zone compatibility. Our nearshore engineers provide flexible, high-quality development support, ensuring smooth project execution with minimal delays.
Offshore Engineers
Leverage a highly skilled and cost-effective engineering workforce from India, offering 24/7 development capabilities, scalability, and expertise across various technologies. Our offshore engineers help businesses optimize costs while maintaining high-quality standards and accelerating project timelines.
 AptaCloud is your trusted Microsoft-certified partner, specializing in delivering a comprehensive range of cloud and infrastructure solutions tailored to meet your business needs. From Microsoft Azure and Office 365 to advanced infrastructure management services, we empower businesses with cutting-edge technology that ensures scalability, security, and operational efficiency. Our expertise extends to implementing, managing, and optimizing Microsoft services, enabling organizations to streamline their operations, enhance productivity, and reduce costs. At AptaCloud, we are committed to providing reliable, secure, and innovative solutions that help businesses thrive in the ever-evolving digital landscape.
AptaCloud is your trusted Microsoft-certified partner, specializing in delivering a comprehensive range of cloud and infrastructure solutions tailored to meet your business needs. From Microsoft Azure and Office 365 to advanced infrastructure management services, we empower businesses with cutting-edge technology that ensures scalability, security, and operational efficiency. Our expertise extends to implementing, managing, and optimizing Microsoft services, enabling organizations to streamline their operations, enhance productivity, and reduce costs. At AptaCloud, we are committed to providing reliable, secure, and innovative solutions that help businesses thrive in the ever-evolving digital landscape.Microsoft
Transform your operations with AptaCloud’s Microsoft-certified solutions, including Azure, Office 365, and Dynamics 365, designed to enhance efficiency and collaboration.
Infrastructure
Optimize your IT with AptaCloud’s secure and scalable infrastructure solutions, offering seamless migration, management, and cost-effective performance.
Consulting & Strategy
Unlock your business’s full potential with expert consulting and strategic planning tailored to your unique growth goals. Our team helps you identify opportunities, streamline processes, and implement effective digital strategies to drive growth and long-term success.
Digital Marketing
Enhance your online presence with data-driven marketing solutions designed to maximize engagement and conversions. From SEO and paid campaigns to social media and content marketing, we create tailored strategies that deliver measurable results and boost your brand’s visibility.
Creative Services
Bring your ideas to life with visually stunning designs and compelling content that resonate with your audience. From branding and UI/UX design to multimedia content creation, we craft engaging experiences that enhance customer interactions and strengthen your brand identity.
- Industries
Healthcare
Transform patient care with advanced digital solutions tailored to healthcare providers and systems
Medical Devices
Accelerate innovation with advanced technology solutions for designing, developing, and ensuring compliance of medical devices.
Pharmaceuticals
Streamline drug development and supply chain management with cutting-edge digital tools.
Banking
Enhance customer experiences and ensure compliance with secure, scalable banking solutions.
Financial Services
Drive growth with intelligent solutions for asset management, fintech, and advisory services.
Insurance
Modernize operations with digital platforms that simplify claims, underwriting, and customer engagement.
Manufacturing
Revolutionize production and supply chains with smart factory and IoT solutions.
Transportation & Logistic
Optimize operations and improve delivery efficiency with advanced logistics technologies.
Expert Coding
We handpick developers to fit your project’s unique requirements, ensuring their skills and expertise align with your goals. You get a dedicated partner focused solely on your success.
Flexible Solutions for All
From startups to global enterprises, our nearshore developers adapt to your specific project requirements, offering tailored solutions that drive success
Full Code Ownership
Our developers adhere to strict NDAs and provide complete transparency, ensuring that you retain full ownership of your code
Aligned Work Hours
Working in US Central time zone, our nearshore developers collaborate during your business hours, enabling real-time updates, seamless communication, and faster turnaround times
First-Time Perfection
Our nearshore developers prioritize delivering the right solution the first time, reducing the need for revisions and helping you launch faster with confidence
Cost-Effective Excellence
Nearshore developers from JumpGrowth combine top-notch quality with cost efficiency, ensuring optimal value for your budget
Ongoing Maintenance & Support
Our nearshore developers don’t stop at delivery because we offer continued support and maintenance to ensure your project’s long-term success
100% Satisfaction Guaranteed
Our nearshore developers go the extra mile to meet and exceed your expectations, ensuring you’re completely satisfied with every project
- About
About Jumpgrowth
JumpGrowth is a digital development studio dedicated to helping businesses shape the future with scalable and innovative digital solutions. As part of OTS Solutions and a registered trademark, JumpGrowth was established in 2018 as a separate brand, focusing on delivering high-quality digital development services for mid-sized businesses and enterprises.
- Services
Product Engineering
Empower your business with cutting-edge digital solutions that drive innovation and seamless customer experiences
Hire
Build your dream team with expert staffing solutions that match top talent to your unique business needs
Cloud
Leverage secure, scalable cloud solutions to streamline operations and unlock new opportunities
Growth
Accelerate your success with tailored strategies and solutions that scale your business efficiently
Artificial Intelligence
Discovery
Onshore Engineers
Gain direct access to top-tier engineering talent in the USA, ensuring seamless collaboration, real-time support, and in-depth industry expertise. Our onshore engineers provide localized solutions tailored to your business needs, enabling faster project execution with minimal communication barriers.
Nearshore Engineers
Benefit from skilled engineering professionals in Mexico, combining the advantages of cost efficiency, cultural alignment, and convenient time zone compatibility. Our nearshore engineers provide flexible, high-quality development support, ensuring smooth project execution with minimal delays.
Offshore Engineers
Leverage a highly skilled and cost-effective engineering workforce from India, offering 24/7 development capabilities, scalability, and expertise across various technologies. Our offshore engineers help businesses optimize costs while maintaining high-quality standards and accelerating project timelines.
 AptaCloud is your trusted Microsoft-certified partner, specializing in delivering a comprehensive range of cloud and infrastructure solutions tailored to meet your business needs. From Microsoft Azure and Office 365 to advanced infrastructure management services, we empower businesses with cutting-edge technology that ensures scalability, security, and operational efficiency. Our expertise extends to implementing, managing, and optimizing Microsoft services, enabling organizations to streamline their operations, enhance productivity, and reduce costs. At AptaCloud, we are committed to providing reliable, secure, and innovative solutions that help businesses thrive in the ever-evolving digital landscape.
AptaCloud is your trusted Microsoft-certified partner, specializing in delivering a comprehensive range of cloud and infrastructure solutions tailored to meet your business needs. From Microsoft Azure and Office 365 to advanced infrastructure management services, we empower businesses with cutting-edge technology that ensures scalability, security, and operational efficiency. Our expertise extends to implementing, managing, and optimizing Microsoft services, enabling organizations to streamline their operations, enhance productivity, and reduce costs. At AptaCloud, we are committed to providing reliable, secure, and innovative solutions that help businesses thrive in the ever-evolving digital landscape.Microsoft
Transform your operations with AptaCloud’s Microsoft-certified solutions, including Azure, Office 365, and Dynamics 365, designed to enhance efficiency and collaboration.
Infrastructure
Optimize your IT with AptaCloud’s secure and scalable infrastructure solutions, offering seamless migration, management, and cost-effective performance.
Consulting & Strategy
Unlock your business’s full potential with expert consulting and strategic planning tailored to your unique growth goals. Our team helps you identify opportunities, streamline processes, and implement effective digital strategies to drive growth and long-term success.
Digital Marketing
Enhance your online presence with data-driven marketing solutions designed to maximize engagement and conversions. From SEO and paid campaigns to social media and content marketing, we create tailored strategies that deliver measurable results and boost your brand’s visibility.
Creative Services
Bring your ideas to life with visually stunning designs and compelling content that resonate with your audience. From branding and UI/UX design to multimedia content creation, we craft engaging experiences that enhance customer interactions and strengthen your brand identity.
- Industries
Healthcare
Transform patient care with advanced digital solutions tailored to healthcare providers and systems
Medical Devices
Accelerate innovation with advanced technology solutions for designing, developing, and ensuring compliance of medical devices.
Pharmaceuticals
Streamline drug development and supply chain management with cutting-edge digital tools.
Banking
Enhance customer experiences and ensure compliance with secure, scalable banking solutions.
Financial Services
Drive growth with intelligent solutions for asset management, fintech, and advisory services.
Insurance
Modernize operations with digital platforms that simplify claims, underwriting, and customer engagement.
Manufacturing
Revolutionize production and supply chains with smart factory and IoT solutions.
Transportation & Logistic
Optimize operations and improve delivery efficiency with advanced logistics technologies.
Expert Coding
We handpick developers to fit your project’s unique requirements, ensuring their skills and expertise align with your goals. You get a dedicated partner focused solely on your success.
Flexible Solutions for All
From startups to global enterprises, our nearshore developers adapt to your specific project requirements, offering tailored solutions that drive success
Full Code Ownership
Our developers adhere to strict NDAs and provide complete transparency, ensuring that you retain full ownership of your code
Aligned Work Hours
Working in US Central time zone, our nearshore developers collaborate during your business hours, enabling real-time updates, seamless communication, and faster turnaround times
First-Time Perfection
Our nearshore developers prioritize delivering the right solution the first time, reducing the need for revisions and helping you launch faster with confidence
Cost-Effective Excellence
Nearshore developers from JumpGrowth combine top-notch quality with cost efficiency, ensuring optimal value for your budget
Ongoing Maintenance & Support
Our nearshore developers don’t stop at delivery because we offer continued support and maintenance to ensure your project’s long-term success
100% Satisfaction Guaranteed
Our nearshore developers go the extra mile to meet and exceed your expectations, ensuring you’re completely satisfied with every project
- About
About Jumpgrowth
JumpGrowth is a digital development studio dedicated to helping businesses shape the future with scalable and innovative digital solutions. As part of OTS Solutions and a registered trademark, JumpGrowth was established in 2018 as a separate brand, focusing on delivering high-quality digital development services for mid-sized businesses and enterprises.